Search Knowledge Base by Keyword
-
Introduction
-
Fundamentals
-
Favorites
-
Dashboards
-
Attachments
-
Reports
-
- Available Reports
- All Asset Types
- Application Certification Status
- Application Discovery
- Application Group Analysis
- App Group to SCCM Collection Analysis
- Application Install Count
- Application License Management
- Application Usage
- Asset Column Mappings
- Asset Count by Property
- Asset Links Count by Asset Type
- Build Sheet
- Computer User Assignment
- Delegate Relationships
- ETL Synch Data
- ETL5 Staging Data
- Migration Readiness (Basic)
- Migration Readiness (Complex)
- O365 License Management
- O365 Migration Readiness
- Patch Summary
- SCCM OSD Status
- Scheduled Computers by Wave
- Scheduled Users by Manager
- User Migration Readiness
- VIP Users
- Wave & Task Details
- Wave Group
- Windows 10 Applications
- Show all articles ( 15 ) Collapse Articles
-
Self Service
-
Workflow
-
Assets
-
- View Asset
- Asset Properties
- Images
- Notes
- Waves
- Tasks
- Attachments
- History
- Rationalization
- QR Code
- Linked Assets
- SCCM Add/Remove Programs
- Altiris Add/Remove Programs
- Related Assets
- Relationship Chart
- Permissions
- Show all articles ( 1 ) Collapse Articles
-
Event Logs
-
Users & Groups
-
Asset Types
-
Charts & Dashboards
-
Options
-
- Modules
- Analytics
- Asset Images
- Asset Rationalization
- Asset Rules
- Attachments
- Bulk Edit
- Data Generator
- Data Mapping
- ETL
- Form Builder
- Multi-Factor Authentication
- Relationship Chart
- Reports
- Self Service
- Single Sign-On
- T-Comm
- Show all articles ( 3 ) Collapse Articles
-
Module Settings
-
-
-
- View Connection
- Connection Properties
- Make Into Connector
- Delete Connection
- Inbound Jobs
- Outbound Jobs
- New Inbound Job
- New Outbound Job
- Enable Job
- Disable Job
- Edit Inbound Job
- Edit Outbound Job
- Upload File
- Run Inbound Job
- Run Outbound Job
- Set Runtime to Now
- Reset Job
- Delete Job
- Job Log
- Show all articles ( 4 ) Collapse Articles
-
-
- View Connector
- Connector Properties
- Authentication Methods
- New Authentication Method
- Edit Authentication Method
- Delete Authentication Method
- Fields
- Edit Field
- Inbound Job Fields
- Edit Inbound Job Field
- Inbound Job Templates
- New Inbound Job Template
- Edit Inbound Job Template
- Delete Inbound Job Template
- Outbound Job Fields
- Edit Outbound Job Field
- Outbound Job Templates
- New Outbound Job Template
- Edit Outbound Job Template
- Delete Outbound Job Template
- Show all articles ( 5 ) Collapse Articles
-
-
- ETL5 Connectors
- Absolute
- Azure Active Directory
- Comma-Separated Values (CSV) File
- Generic Rest JSON API
- Generic Rest XML API
- Ivanti (Landesk)
- JAMF
- JSON Data (JSON) File
- MariaDB
- Microsoft Endpoint Manager: Configuration Manager
- Microsoft SQL
- Microsoft Intune
- Oracle MySQL
- PostgreSQL
- Pure Storage
- ServiceNow
- Tanium
- XML Data (XML) File
- Show all articles ( 4 ) Collapse Articles
-
-
API & Stored Procedures
-
Administration
-
FAQs
New Authentication Method
< Back
From the Authentication Methods tab, you can create authentication methods. To create:
- Click the New Authentication Method button to bring up the New Authentication Method dialog
- Enter the properties of the new authentication method
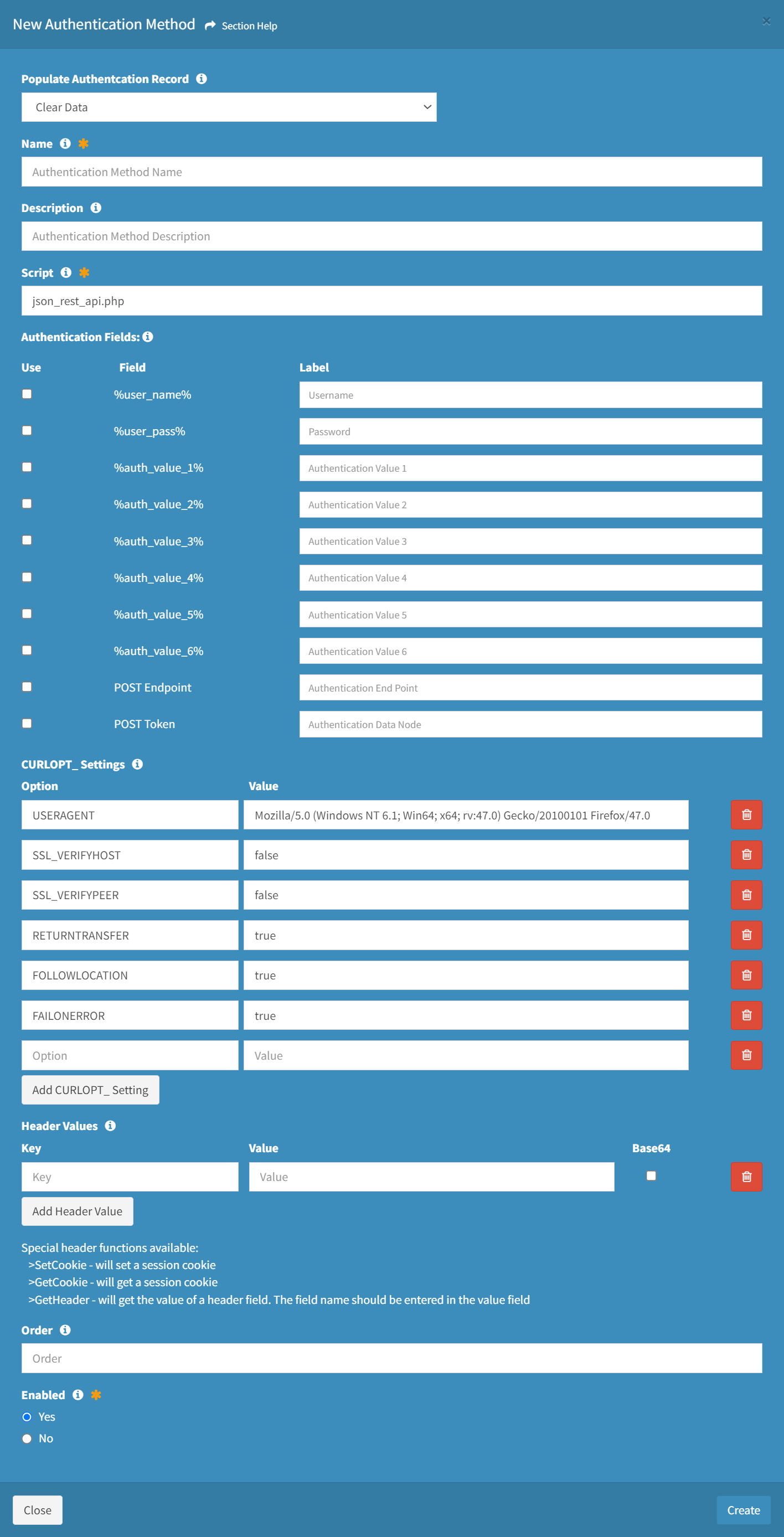
- Populate Authentication Record – Choose how to populate the authentication method (required)
- Clear Data – Start with an empty record
- Clone Authentication Method – Start with a clone from an existing authentication method
- Name – Name of the authentication method (required)
- Description – Description of the authentication method (optional)
- Script – Name of the authentication script (required)
- json_rest_api.php
- Authentication Fields – Authentication fields of the authentication method (optional)
- CURLOPT Settings – CURLOPT settings of the authentication method (optional)
- Header Values – API header values of the authentication method (optional)
- Data Values – API data values of the authentication method (optional)
NOTE: These settings are only visible when POST Endpoint has been checked. - Post Authorization CURLOPT Settings – Post authorization PHP CURLOPT settings of the authentication method (optional)
NOTE: These settings are only visible when POST Endpoint has been checked. - Post Authorization Header Values – API post authorization header values of the authentication method (optional)
NOTE: These settings are only visible when POST Endpoint has been checked.
- json_rest_api.php
- Order – Order of the authentication method in the menu (optional)
- Enabled – Choose if the authentication method is enabled (required)
- Populate Authentication Record – Choose how to populate the authentication method (required)
- Click the Create button when finished to create the authentication method. You will be redirected back to the Authentication Methods tab. Click the Close button to cancel the operation.
- The new authentication method function is only available to users in the Administrator security group

