Search Knowledge Base by Keyword
-
Introduction
-
Fundamentals
-
My ReadyWorks
-
Analytics
-
-
-
- Available Reports
- All Data Types
- Application Certification Status
- Application Discovery
- Application Group Analysis
- App Group to SCCM Collection Analysis
- Application Install Count
- Application License Management
- Application Usage
- Data Type Column Mappings
- Record Count by Property
- Data Links Count by Data Type
- Build Sheet
- Computer User Assignment
- Delegate Relationships
- ETL5 Staging Data
- Migration Readiness (Basic)
- Migration Readiness (Complex)
- O365 License Management
- O365 Migration Readiness
- Patch Summary
- SCCM OSD Status
- Scheduled Computers by Wave
- Scheduled Users by Manager
- User Migration Readiness
- VIP Users
- Wave & Task Details
- Wave Group
- Windows 10 Applications
- Show all articles ( 14 ) Collapse Articles
-
-
-
-
Orchestration
-
Data
-
-
- View Primary Data
- Record Properties
- Images
- Notes
- Waves
- Tasks
- Attachments
- History
- Rationalization
- QR Code
- Linked Records
- SCCM Add/Remove Programs
- Altiris Add/Remove Programs
- Related Records
- Advanced Search
- Relationship Chart
- Primary Data Permissions
- Show all articles ( 2 ) Collapse Articles
-
Integration
-
-
-
- View Connection
- Connection Properties
- Make Into Connector
- Delete Connection
- Connection Error Settings
- Inbound Jobs
- Outbound Jobs
- New Inbound Job
- New Outbound Job
- Job Error Settings
- Enable Job
- Disable Job
- Edit Inbound Job
- Edit Outbound Job
- Upload File
- Run Inbound Job
- Run Outbound Job
- Set Runtime to Now
- Reset Job
- Delete Job
- Job Log
- Show all articles ( 6 ) Collapse Articles
-
-
- View Connector
- Connector Properties
- Authentication Methods
- New Authentication Method
- Authentication Method Error Settings
- Edit Authentication Method
- Delete Authentication Method
- Fields
- Edit Field
- Inbound Job Fields
- Edit Inbound Job Field
- Inbound Job Templates
- New Inbound Job Template
- Job Template Error Settings
- Edit Inbound Job Template
- Delete Inbound Job Template
- Outbound Job Fields
- Edit Outbound Job Field
- Outbound Job Templates
- New Outbound Job Template
- Edit Outbound Job Template
- Delete Outbound Job Template
- Show all articles ( 7 ) Collapse Articles
-
-
- ETL5 Connector Info
- Absolute
- Azure Active Directory
- Comma-Separated Values (CSV) File
- Generic Rest JSON API
- Generic Rest XML API
- Ivanti (Landesk)
- JAMF
- JSON Data (JSON) File
- MariaDB
- Microsoft Endpoint Manager: Configuration Manager
- Microsoft SQL
- Microsoft Intune
- Oracle MySQL
- PostgreSQL
- Pure Storage
- ServiceNow
- Tanium
- XML Data (XML) File
- JetPatch
- Lenovo XCLarity
- Nutanix Move
- Nutanix Prism
- Nutanix Prism - Legacy
- RVTools
- Simple Object Access Protocol (SOAP)
- VMware vCenter
- VMware vCenter SOAP
- Show all articles ( 13 ) Collapse Articles
-
-
Admin
-
-
-
- Modules
- Attachments
- Bulk Edit
- Data Generator
- Data Mapping
- Data Quality
- ETL
- Form Builder
- Images
- Multi-Factor Authentication
- Notifications
- Rationalization
- Relationship Chart
- Reports
- Rules
- Single Sign-On
- T-Comm
- User Experience
- Show all articles ( 4 ) Collapse Articles
-
-
API
-
Administration
-
FAQs
-
Solutions
Malware
< Back
The SCCM Malware page provides a view into your malware infections detected by SCCM.
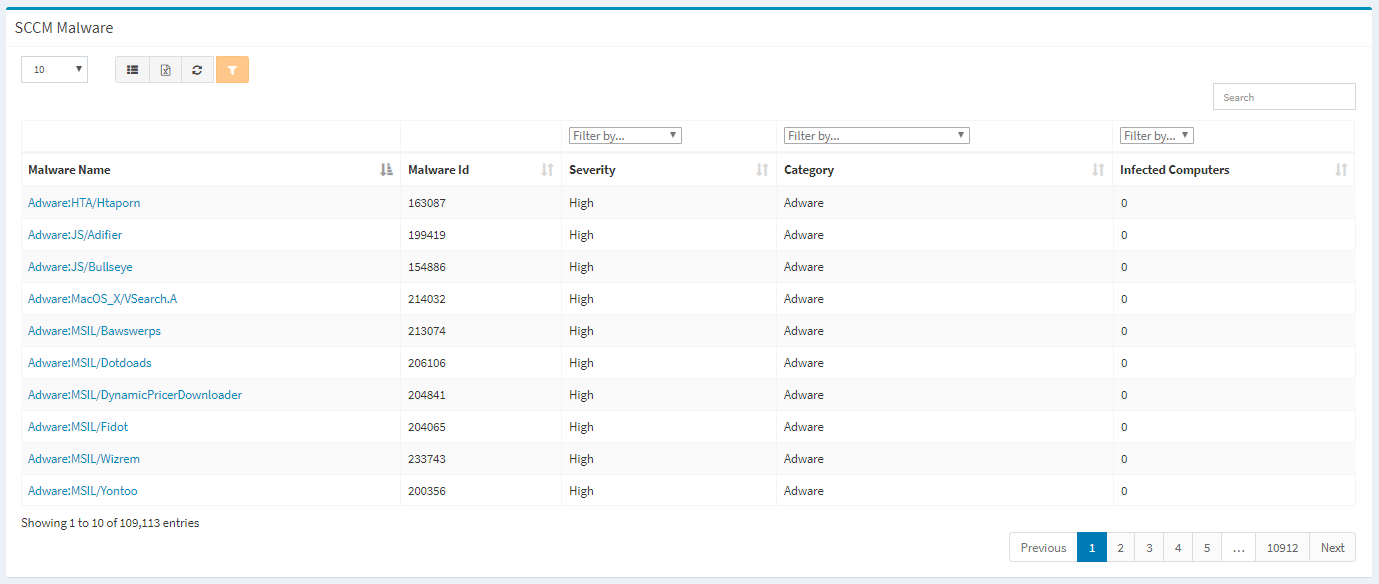
Available operations:
- View a list of malware infections detected by SCCM
- Columns available
- Malware Name – Name of the malware
- Malware Id – SCCM Id of the malware
- Severity – Severity of the malware (High, Low, Medium, Not Yet Classified, Severe)
- Filter by High, Low, Medium, Not Yet Classified, Severe
- Category – Category of the malware (e.g. Adware, Spyware, etc.)
- Filter by category
- Infected Computers – Number of computers infected by the malware
- Filter by common values
- Columns available
- View the properties of malware by clicking the hyperlink of the Malware Name field
- You can also change the number of visible rows in the table, set column visibility, export to CSV or Excel, refresh the table, and search for text
Accessing
From the SCCM Asset dashboard, you can drilldown into your SCCM malware to see additional details. To drilldown:
- Click the More Info hyperlink on the Malware widget to drilldown. You will be redirected to the SCCM Malware page.
View Malware
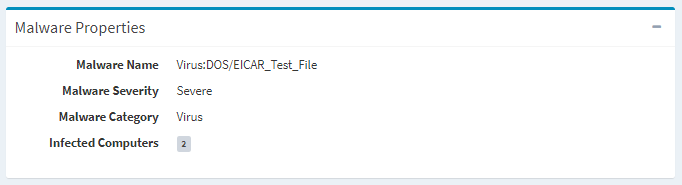
The View Malware page provides the ability to view the properties of a malware infection and is accessed by clicking the hyperlink of the Malware Name field of a malware infection.
Available operations:
- View the properties of the malware infection
- View the computers infected by the malware
Malware Properties – View the properties of the malware infection
Infected Computers – View the computers infected by the malware
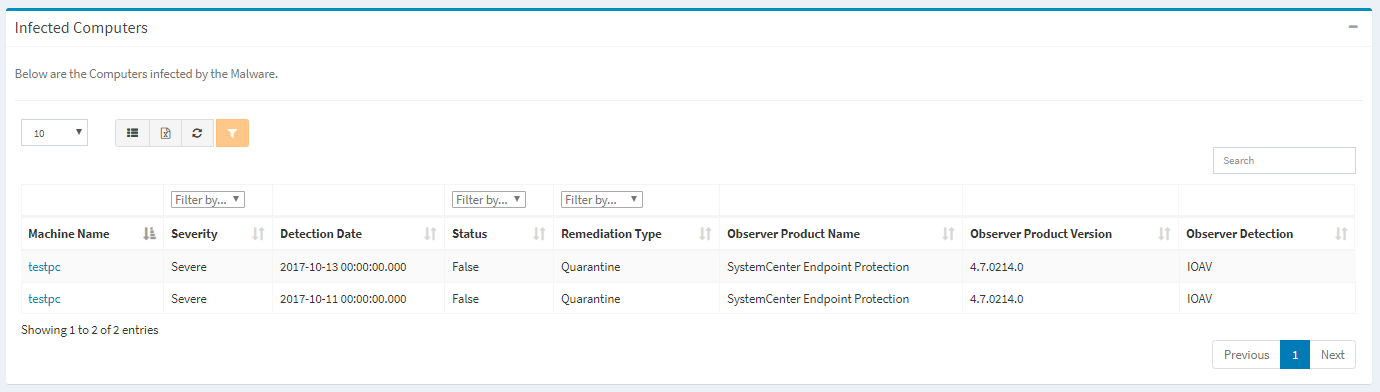
An informational message is displayed if there are no computers infected by the malware.


